Qu’est-ce que l'administration de la gouvernance des identités ?
Dans le monde numérique actuel, la sécurité et la confidentialité des données sont des préoccupations majeures pour les entreprises et les organisations. La gestion des identités et des accès est un aspect crucial de cette sécurité, car elle permet de contrôler qui a accès à quelles ressources et comment ces accès sont utilisés.
L'administration de la gouvernance des identités (IGA) consiste à mettre en œuvre une structure et des processus pour gérer les identités, c’est-à-dire les informations personnelles et professionnelles des individus, ainsi que leurs droits d’accès aux ressources de l’organisation. Cette gouvernance est essentielle car elle permet de :
- Contrôler qui a accès à quelles ressources
- Assurer la sécurité et la confidentialité des données
- Réduire les risques liés à la perte ou au vol d’informations sensibles
Composants clés
- Identités et attributs
- Mécanismes d’authentification et d’autorisation
- Politiques de gestion des accès
- Intégration avec les systèmes et les applications
- Rapports et surveillance
- Provisionnement des utilisateurs par rôle, département ou autre groupement
- Gestion des privilèges d’accès aux systèmes et aux applications
- Contrôle d’accès basé sur les rôles (RBAC)
- Connexion unique (SSO) pour les utilisateurs
- MFA pour renforcer la sécurité

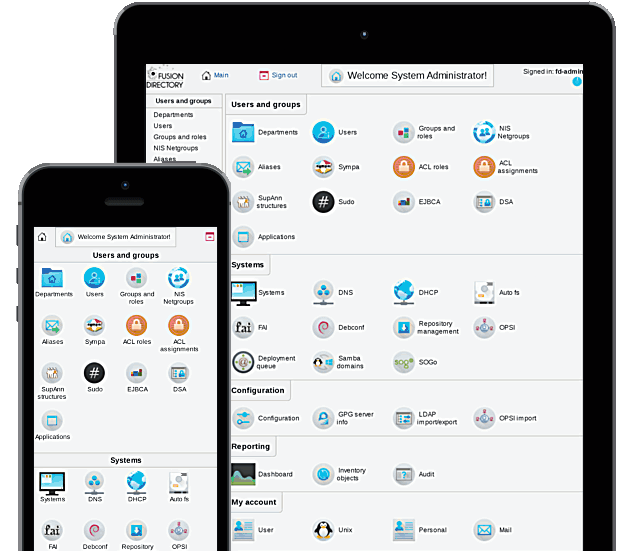
FusionDirectory
Une solution complète, facile à utiliser et souveraine
FusionDirectory est une solution logicielle open source sous licence GPL qui s’inscrit parfaitement dans cette démarche d'administration de la gouvernance des identités. Basée sur le protocole LDAP, FusionDirectory permet de centraliser la gestion des comptes utilisateurs, des groupes, des rôles et des droits d’accès à différentes ressources (serveurs, applications, etc.).
Nos Services
Découvrez l'ensemble de nos services associés :
Audit et analyse de la gestion d'identité et des accès
Permet de prendre du recul sur votre processus de gestion des identités et des accès actuel et d’identifier des axes d’amélioration.
Modernisation de votre gestion d'identité et des accès
Définition des spécifications fonctionnelles et techniques, déploiement et configuration des services.
Formations
Suivez nos formations afin d'acquérir les bonnes pratiques d'administration des services de gestion des identités et des accès.
